This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognising you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Phishing scams: a cybercrime challenge

Phishing remains one of the favorite weapons of cybercriminals usually carried out through email and social media or mobile phone texts. They are quick to adapt to current events in real time like new business support schemes or tax repayments. Phishing scams can be very sophisticated, with images and language that look very convincing, and cybercriminals are constantly redoubling their inventiveness to steal other people’s money and data. Here we give the basic facts on phishing so you can protect yourself.
What is phishing?
Phishing is a form of cybercrime in which the potential victim receives a link via email, text message or other digital tools from a scammer posing as someone else. They often pose as your bank, energy supplier, national tax office or a technology company providing your services. If the link is accessed, the scammer can gain some access to important financial and business data.
The goal is to “phish” (or fish) sensitive data, such as business and personal information, passwords, credit cards or credit card data. Once the data is accessed the fraudster is able to access the main accounts of the victim and steal money or take over their identity to take out loans etc.
Phishing styles and methods
Emails are still the most common method of phishing. It may appear in your account from someone posing as your bank warning you of a breach on your account and asking you to confirm your identity via a link or by opening an attachment.
The link will invite you to complete a counterfeit web page which take your information, opening the attachment could infect your device with malware. It might be from a tech company that you have an account with.
Here’s an example of a phishing email allegedly from Apple.
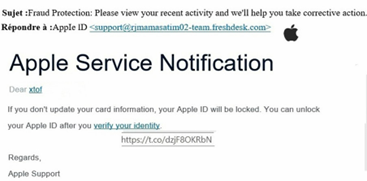
Things to look out for: The email address which is obviously not an official Apple address. If you hover the mouse arrow on the link “verify your identity” it shows a shortened link instead of a recognisable URL for Apple.
Smishing: via SMS or instant messenger apps
Messages are sent via a SMS or instant messaging apps such as WhatsApp or Facebook Messenger which contain a warning (e.g. or “Pay now or your account will be blocked”) or an offer (e.g. “Win a voucher at Aldi”), which encourages you to click on a link or dial a phone number. The link installs malware or directs to a counterfeit web page on which you are asked to input your payment data.
Be aware that legitimate companies are now very cautious in sending out these types of messages.
Things to look out for: hover over the link to the URL to see what it shows up, if it is unfamiliar or doesn’t link to the recognised site it is suspicious.
Phone phishing
This type of phishing scam involves a scammer calling a victim to try to convince them to share personal, financial or security data. They may pose as a partner or collaborator of a major technology company calling you to warn you of a problem with your computer such as a virus or hack, and encouraging you to download a program or click a link to deal with the problem.
If successful, this gives the fraudster access to your computer, and charges a fee to solve the “problem” they have found.
Social networks
Many people now publicly express dissatisfaction via social media, in the hope of getting quick results from the company at fault. Fraudsters quickly create fake accounts and react to the complaint as if they were the customer service department of the company in question. They invite you to offer a link to solve your issue which then leads to malware or data exposure.
Calendar invites
Scammers have been found to send fake invitations to Google Calendar users which contain phishing links. Scammers take advantage of a setting that is enabled by default in Google Calendar and ensures that each calendar invitation is automatically added to your calendar. To prevent malicious invitations from appearing in your calendar and you accidentally clicking on links in those invitations, it’s best to disable this setting.
QR codes
This scam is more likely to occur when you are selling an item, for example on a second-hand marketplace. A scam buyer will offer to make a payment and requests the seller’s account details, which the scammer will then confirm via a request to confirm the details via scanning a QR code. However, scanning the QR code, in combination with the account information the scammer already has will give them direct access to the buyer’s bank account.
Be cautious
If you experience any of these phishing scenarios, be extremely cautious and avoid engaging with the messages and clicking links. Euroconsumers members are campaigning for better systemic solutions from the banks to better protect small businesses and consumers:
- Requiring additional confirmation when large amounts of money are being transferred to give opportunity to cancel transactions that a person may not be aware of.
- Mandate two factor authentication from a different device so that if a scammer has accessed your log in details, they are not easily able to log in on their own device and access the account.
- Reverse password authentication from the bank. Customers are used to being asked their password to authenticate who they are with their bank. The reverse can also help avoid scams, with banking sites being required to reveal that they are indeed your bank and not a fraudulent site.
- IBAN verification: this layer of security is already in operation in the Netherlands. It requires matching the name of the account holder to the IBAN number, in the event that you are a victim of phishing, it will be much easier to spot sa the name and IBAN will not match.
- One-time digital credit card: this involves creating a separate digital credit card containing the exact amount that you intend to spend online, this offers some protection as it limits the amount that can ever be accessed.


